ZStack Cloud Platform
Single Server, Free Trial for One Year
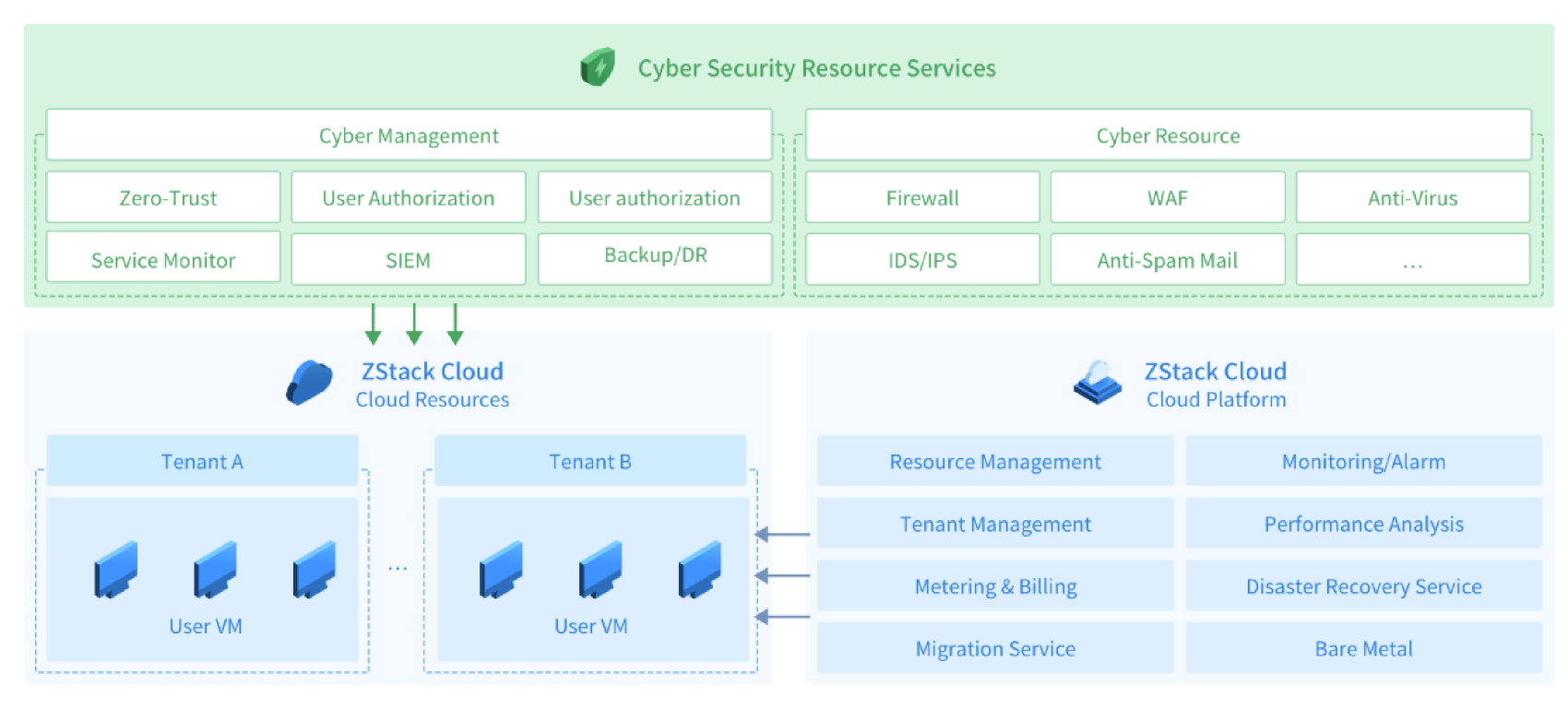
The ZStack security solution meets the cloud users’ needs for virus protection, access control, intrusion detection, intrusion prevention, and virtual patching. It also offers capabilities such as integrity monitoring, log auditing, asset management, vulnerability risk management, detection and response, baseline inspection, and host resource monitoring. This comprehensive solution helps customers build a multi-layered, all-encompassing security defense system.

Address vulnerabilities without needing to reboot servers, ensuring smoother security protection. Supports hotfixes and zero-day vulnerabilities for more timely security measures. Allows for custom patch rules, providing more controllable security protection.

Deep integration with the ZStack Cloud platform eliminates the need to install clients on each cloud host, reducing resource demands for protection. It also supports security protection during cloud host startup intervals.

Meets the CWPP model requirements for cloud host security protection, allowing for the construction of comprehensive security strategies that integrate pre-event, in-event, and post-event protection as needed.
Through the virtual patching technology in ZStack’s cloud host security protection solution, system patches can be applied without downtime. This avoids the need for a system reboot for patch activation, as is common with traditional vulnerability repair methods. This solution ensures business continuity while addressing vulnerabilities.

This solution employs agentless protection technology, eliminating the need to install protection clients on each cloud host. Instead, an antivirus system is deployed on each host machine, allowing for virus protection and removal through the virtualization layer. This effectively reduces resource usage on each cloud host and prevents resource demand spikes during virus scanning.

For scenarios such as security compliance, major event protection, and more, comprehensive needs like cloud host security hardening, log auditing, attack analysis, and tracing can be addressed. By configuring advanced functional modules, personalized protection solutions can be designed to ensure comprehensive cloud host security.

When building a data center cloud platform, the ZStack cloud host security protection solution can be deployed simultaneously. This solution offers features such as virus protection, intrusion detection, virtual patching, and web reputation. It achieves comprehensive proactive defense through security policies.
The ZStack cloud host security protection solution is equipped with a vast virus signature database and an intrusion attack behavior database. This supports users in temporarily deploying the solution to assist in virus analysis and removal when a virus infection is detected or suspected. It can promptly address malicious attacks and reduce the damage caused by such incidents.
The ZStack cloud host security protection solution supports post-attack investigation and traceability. When a cloud host is attacked, the corresponding security function module automatically records attack events and operation logs, providing a basis for subsequent attack path tracing and host security reinforcement. This makes responding to and investigating attacks simpler and more efficient.